Credentials and secrets management often focus on passwords. But there are also other credentials, like SSH keys, that serve the same purpose as passwords in the sense that they are access credentials just as well and, at the same time, are overlooked.
Contents
Why should you pay more attention to your SSH keys?
Vaulting private SSH keys to a central PAM system
Vaulting authorized keys into a central system (LDAPify)
Vaulting encryption keys is a bad way to manage them
From more ways to the best way to manage encryption keys
 There are important reasons why enterprises should pay more attention to keys, including:
There are important reasons why enterprises should pay more attention to keys, including:
- Most passwords are in ‘regular’ use, granting access to targets like Microsoft 365. A subset of passwords grants access to critical infrastructures, company databases, or code repositories, but SSH keys almost always grant access to something critical, since they are used by super admins, power-users, database admins, or maintenance engineers to access credit card databases, energy infrastructures, or company IPR to name a few.
- Up to 80% of critical connections in big enterprises are automated between applications, machines, and systems and run by the SSH protocol. More often than not, these credentials (SSH keys) are mismanaged or not managed at all.
- Keys are part of the compliance checklist within the Identity and Access Management category.
- SSH keys typically outnumber passwords in large enterprise networks by a ratio of 10 to 1.
- SSH keys are used to bypass security controls, like privileged access management (PAM) solutions.
Unfortunately, many companies are oblivious to the SSH key problem, let alone to the best ways to manage their keys. This is not a surprise. Many PAM solution providers, who claim to manage SSH keys, fail to do so at an acceptable level. Traditional PAM solutions were built to manage passwords, but the same password vaulting approach just doesn’t work with keys.
Let’s explore a couple of typical ways that attempt to manage keys using key vaults.
Vaulting private keys to a central PAM system
Most PAM solutions try to vault encryption keys such as SSH keys. But SSH keys are functionally different, and therefore you cannot handle them like passwords.
Here are three top reasons why PAM tools fail in vaulting SSH keys:
- Vaulting SSH keys requires changes to tools and scripts and often requires the hire of professional services to migrate tools and systems to use private keys from a centralized vault.
- Anyone with sufficient IT skills can create an SSH key pair anywhere regardless of the private key vault. Hence, the aforementioned PAM bypass.
- A PAM tool might not have the capabilities to automate SSH key management tasks such as key deployments, rotations, and automatic key removals. This is a massive burden for the team responsible for managing keys.
Vaulting authorized keys into a central system (LDAPify)
LDAP (Lightweight Directory Access Protocol) can be used to store users' public key(s) and an SSH server that is customized to obtain authorization upon authentication from LDAP.
Some of the shortcomings of this approach include:
- It does not support the discovery and inventory of existing private and authorized keys on systems.
- It does not provide an overview of trust relationships created by existing SSH keys, e. g. how many targets can be accessed with a single key.
- It lacks mechanisms to evaluate existing keys against policies such as established security standards and recommendations.
Vaulting SSH keys is a bad way to manage them
To cut a long story short, we recommend leaving the keys where they are and managing them at their native locations, instead of using key vaults. Vaulting keys requires making changes to the scripts and configurations you have set up for your environment, making change management a nightmare.
What’s more, solutions like traditional PAMs were not built to manage and vault SSH keys. We know this, since all our key management customers have a traditional PAM installed but found the solution wanting. Learn more about why traditional PAMs fail to manage SSH keys in our white paper.
From vaulting to the best way to manage SSH keys
There are naturally more ways to manage SSH keys than vaulting them, and I know you are itching to learn more. Luckily, we have just the piece for you. Just read this document to learn about the good, the bad, and the ugly ways to manage SSH keys.
At the end of the day, there is a stand-out solution to manage keys: our Zero Trust Suite. It manages the keys where they are, doesn’t require reconfiguring your scripts or configurations, finds hard-to-find keys along with their configuration files, and automates a ridiculous amount of manual work.
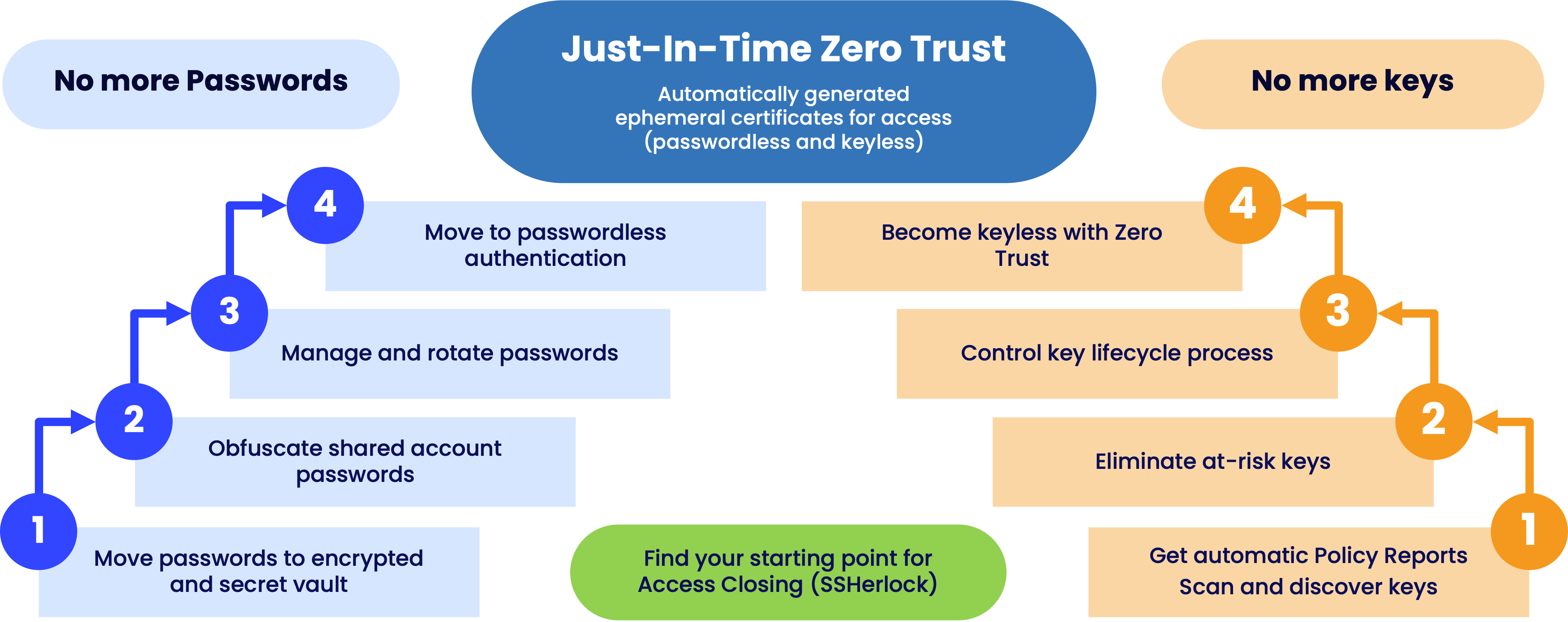
But you can take it a step further. Managing keys is good but you are better without having to manage them at all. You can migrate to a keyless approach in your management efforts, using an iterative approach illustrated in the image.
In fact, we suggest you manage your passwords AND keys with Zero Trust Suite which not only gives you control over your credentials but also helps you get rid of them with a passwordless and keyless approach.
Learn more about the best way to manage passwords here >>>
Jani Virkkula
Currently employed by SSH.COM as Product Marketing Manager, Jani is a mixed-marketing artist with a strong background in operator and cybersecurity businesses. His career path of translator->-tech writer -> marketer allows him to draw inspiration from different sources and gives him a unique perspective on all types...