Beyond strong identity for critical and sensitive communications in any environment
SSH Zero Trust Suite is a modular software suite that allows companies to communicate securely in traditional on-premise environments, when migrating to the cloud - and at any stage in between. It works well in IT, industrial OT and multi-protocol environments.
Our Suite secures communications up to a quantum-safe level when:
- applications, systems, sites, machines or data centers need to connect
- humans share sensitive data with each other
- experts need to access critical targets for updates, production environment uploads, maintenance or configurations
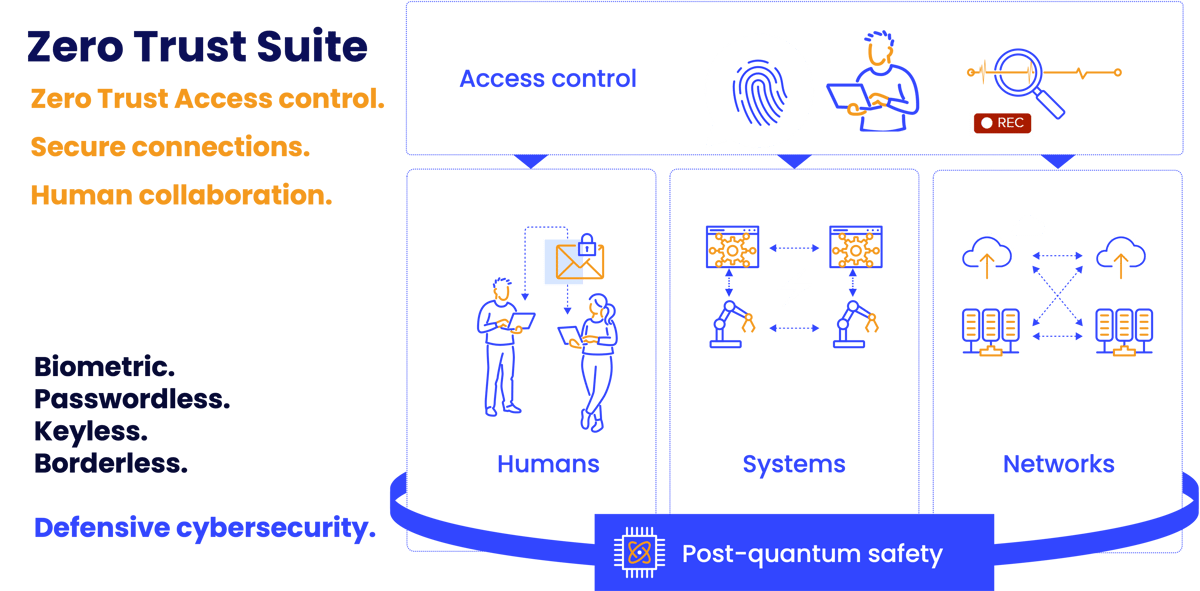
Identify. Restrict. Authorize. Control.
Ensure every access and connection is authenticated with a strong (biometric) identity. Grant access only to the right target from a single solution. Assign only the minimal level of privilege needed to get the job done.
Prevent risks from materializing and mitigate the likelihood of data leaks and breaches with a defensive cybersecurity mindset.
Audit. Monitor. Record.
All sessions are audited, tracked, monitored, and recorded as needed for forensics, compliance, and learning. Turn on alerting, enjoy dashboards, generate reports, and detect anomalies and risks with AI-based User and Entity Behavior Analytics (UEBA).
Integrate with your existing security architecture
Integrate to Security Information and Event Management (SIEM) and Security Operation Center (SOC) for vulnerability management and threat intelligence.
Map user roles with identities with easy integration to Identity and Access Management (IAM), Identity Management (IdM), or directory services (like Microsoft Entra ID). Stay up-to-date on any changes between them.
Protect on-prem, hybrid, and cloud environments alike
Secure communications in both traditional and modern technological environments in IT and OT. Migrate to modern secure communications driven by the cloud while protecting your investment in the traditional installed base, including mainframes. Use a single hybrid solution for all.
Book a demo to find out more.
Share, transmit, and store sensitive information securely
Sensitive data, like medical records, government secrets, or personally identifiable information (PII), should only be shared with solutions purpose-built for the task. Build authorized secure communications channels and workspaces across and outside your own organization.
Identify and secure automated connections
Identify and secure connections between data centers, industrial systems, applications, sites, clouds – or any combination between them.
Learn how to secure machine-to-machine connections and their credentials >>>
With or without permanent credentials. You choose.
Manage, vault, and rotate your passwords and authentication keys when necessary. Then get rid of the pain, costs, and complexity of having to manage them.
Start your journey toward passwordless and keyless authentication with us. Move to just-in-time ephemeral (short-lived) certificates.
Secure your future with quantum-safe connections
Protect your business from existing and future threats with a proven-in-use and future-proof portfolio and core competence.
Take a quantum leap in secure communications with our quantum-safe solutions. Stop data harvesting, unsecure file sharing or mainframe communications.
Customer case examples
Operational Technology (OT)
Maritime engine diagnostics access from the IoT cloud for the fleet
-
SSH/RDP access to marine vessels over a satellite link anywhere in the world
-
Zero Trust Suite provides tracking of user identities and a transparent view into the sessions, securing the VPN tunnel from unsanctioned use
Remote and on-site access for maintenance engineers of the seaport infrastructure
-
RDP and HTTP(S) connectivity to on-target remote terminals running programmable logic controller (PLC) systems to control seaport operations
-
Strong identity authentication combined with role-based access to data centers for in-house and third-party engineering staff
-
Zero Trust role-based VPN access to PLC units and other IP targets (in development)
Passwordless and keyless authentication and access
British universal bank prevents security control bypass
-
Compliance requirement for controlling SSH keys alongside passwords to prevent privileged access management (PAM) bypass
-
1.5 million keys renewed automatically by application owners
-
Zero Trust Suite reduced the biggest risk of shared passwords by migrating to JIT ephemeral certificates for passwordless and keyless access
Global semiconductor company fixes a security audit failure
-
Risk assessment and scanning done with our SSH Risk Assessment tool reported access credential (SSH key) violations
-
Keys-violating global SSH policy removed
-
Application-to-application (A2A) access controlled with JIT SSH certificate access for keyless authentication
-
Passwordless authentication for secure remote user access
Secure human-to-human communications and data and file sharing
Blood donation with data encryption and protection
-
Donor data and identity is protected when they fill in the donor form
-
Sending the donor data only to authorized personnel with strong encryption and sender/recipient verification
-
Blood type shared with operating doctors in a secure workspace
A financial institution establishes authorized channels for sharing, storing, and collecting confidential business data over the internet
-
Data is stored securely in an encrypted format with strict access management and user authentication to minimize errors or indiscriminate access
-
Access levels to data align with the sensitivity level (confidential, restricted, secret) of each investment and funding deal
-
Multiple communication options, structured data, digital signatures, and audit logs of activities
Secure data and file sharing
European railway company updating their ticketing system to meet PCI-DSS compliance
-
Secure application traffic containing credit card data to meet PCI-DSS requirements runs over Network Address Translation (NAT) enabled firewalls
-
Train ticketing machines all around Europe send credit card data securely for further processing
-
No changes to the existing system
ERP company secures data communications in its internal network
-
Lowered total cost of ownership compared to in-house maintained system
-
Strong authentication (with Kerberos)
-
Robust communications architecture built together with responsive support services
-
Windows-based servers improved interoperability with third-party Secure Shell implementations
legacy
 Perimeter security
Perimeter security
modern
 Hybrid cloud
Hybrid cloud
Vaults and keyless
Firewalls/VPNs and Zero Trust
best-in-class
 Zero Trust
Zero Trust
Keyless + passwordless
Automated + immutable
SSH products behind the Zero Trust Suite
SSH Zero Trust Enterprise Key Management
Start your migration to the future of Secure Shell connections without SSH keys in large and heavily regulated enterprise environments.
PrivX Hybrid Privileged Access Management
Easy, automated, and cost-efficient way to manage access to critical data in the hybrid cloud, DevOps repositories, network devices, databases, or industrial target systems.
Tectia File Sharing and Tunneling
Tectia Zero Trust Edition turns your SFTP server or a cluster of servers into a modern batch and bulk file sharing server with advanced features, like quantum-safe connections, role-based access control, full audit trails, AD/LDAP integration, and a web client interface.
More about Tectia Zero Trust>>>
SSH Secure Collaboration 2024
SSH Secure Collaboration is a secure business communication solution that helps organizations and employees access, verify, sign, receive, store, and share sensitive data in an extra secure and compliant manner across organizational borders and when working with external stakeholders
More resources on Zero Trust
Unlock the secrets of Zero Trust: because trusting no one is the new cool. Here are some extra resources.
WHITE PAPER: The Future of Cybersecurity is Passwordless and Keyless
Get the white paper
GUIDE: A Comprehensive Guide to Zero Trust Architecture
Read the guide
SOLUTION BRIEF: Zero Trust Suite for Secure Communications and Access
Read the solution brief
GUIDE: Zero Trust Enterprise SSH Key Management
Get the guide
VIDEO: Zero Trust - Passwordless and Keyless Access to Vital Data and Systems
Watch the video
BLOG POST: Passwordless and Keyless SSH - How to Migrate to Zero Trust SSH Access?
Read the blog post
Contact us for a demo.
Fill in the form and see the PrivX Zero Trust Suite in action >>>





