modern and future-proof privileged access management
How does PrivX PAM3 work?

From identity to the target securely
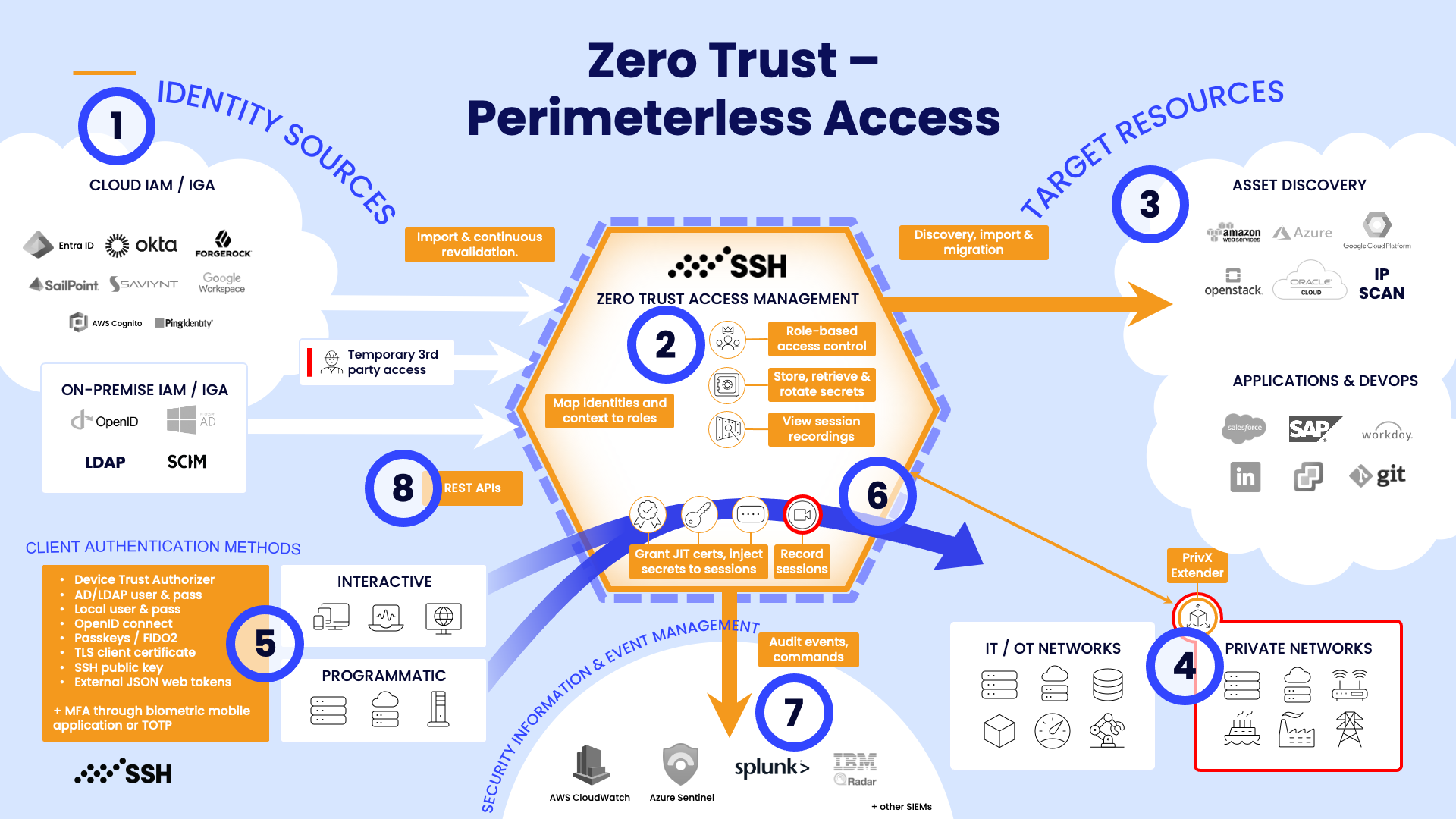
1. IAM/IGA integration
Users and user groups are maintained and governed in identity and access management (IAM/IGA) systems. These systems contain up-to date information about who (identities/users/group) are authorized to access what and when. PrivX also has a local user directory which can be used independently of IAM/IGA systems.
2. Role-based access control
PrivX links the user information containing the right identity and authorization to the right role. Therefore, all access to critical targets is granted using role-based access controls (RBAC). Since roles rarely change, and the link between the role and identity is always up-to-date. Governance can be done in addition to IAM/IGA with build-in workflow function (request/approval).
3. Target resources
Access management to all your mission-critical targets are under a single pane of glass, be they servers, multi-cloud hosts, data centers, network infrastructure, web applications, network devices, databases or management consoles.
PrivX employs an agentless approach to manage privileged access, which means it doesn't require installing and maintaining software agents on target systems. Targets can automatically be imported from cloud providers such as Amazon Web Services, Microsoft Azure, Google Cloud, or from virtualisation environments such as OpenStack. Targets can also be pushed in to PrivX via APIs or SCIM by using our custom SCIM protocol extension.
4. PrivX Extender
A PrivX Extender is a component of the PrivX system that facilitates secure connections to target hosts that are not directly accessible by PrivX. It acts as a relay (reverse proxy), allowing PrivX to reach hosts located in separate, protected networks, such as those without public IP addresses
5. Just-in-time access
When the user logs in to the browser-based PrivX UI (using SSO and MFA if needed), she can only see and select the targets available to her restricted by her role. The user doesn't handle or see any access secrets at any point, but the authentication is done automatically in the background and access is granted just-in-time. The secrets needed for the connection are baked into ephemeral certificates which expire automatically after establishing the session, leaving no secrets behind. Native client can be used as well.
6. Certificate based authentication
In addition to vaulting and rotating secrets, target system authentication can be done with unique ephemeral certificates. In ephemeral certificate-based authentication, the target systems are accessed without the need for permanent access credentials, explicit access revocation or traditional SSH Key management.
For each session, a short-lived (ephemeral certificate) is issued just-in-time. Method is based on various industry-standards.
7. Session recording and audit events
Sessions can be recorded and monitored real-time. PrivX collects detailed records of actions and occurrences within the system, providing a comprehensive trail for security and compliance purposes. These audit events include various types of activities, such as user logins, configuration changes, and system errors. This information can be automatically sent to external systems (i.e. SIEMs) for alerting and reporting
8. REST APIs
Applicaton Programming Interfaces (API)/Software Development Kits (SDK) can be used for customized integrations. Examples of these include integrations to ticketing systems, behavior analytics solutions and Information technology service management (ITSM).