What we do
UNIVERSAL SSH KEY MANAGER®
Enterprise Key Management (EKM)
Universal SSH Key Manager® (UKM) is a Zero Trust SSH key management solution that automates governing of SSH keys according to compliance and security standards, and manages and automates the lifecycle of encryption keys for risk mitigation and audit success.
NQX™ & Tectia®
Quantum-Safe Cryptography (QSC)
Defend your long-term secrets against the quantum threat with quantum-safe cryptography (QSC) and quantum security solutions. NQX for transporting Ethernet and IP traffic across any network, and Tectia Quantum-Safe Edition for secure remote access, file transfer, and tunneling.
Secure collaboration
Secure business communications & data security
Secure Collaboration Suite maintains and protects your sensitive and confidential data when stored and shared. Your emails, signatures, web forms, and shared files are protected with a high level of security and robust encryption that also meets strict regulatory requirements like GDPR.
Our services & support
SSH Risk Assessment™
A non-intrusive service to determine what security risks and vulnerabilities exist due to SSH Keys. Mitigate SSH Key risk, gain compliance and pass your audit.
Professional Services
We can help you with the whole solution lifecycle from architectural design and planning to smooth deployment and support for your daily operations.
Customer support
We offer up to 24/7 enterprise support and global coverage for customers of SSH.COM commercial software. Our team of experts is always happy to help.
Contact us
Do you have questions about our products or services? Would you like find out about pricing, POC or an enterprise demo? Don't be shy: get in touch and let's talk!
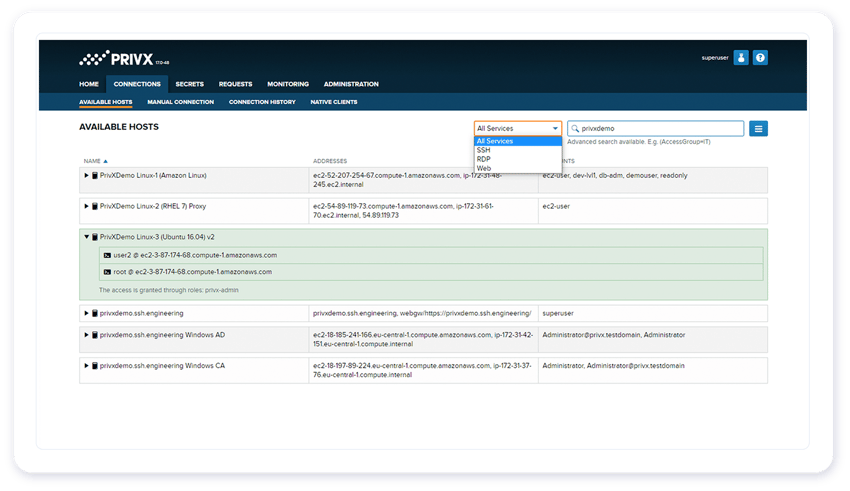
Just-in-time access with just-enough privilege for critical targets
Secure access to all your critical targets from one solution, be the target servers in hybrid IT environments, network devices, databases, applications, or production sites.
Accelerate the joiners, movers, and leavers process by automating the linking of the right identity with the right role. Ensure that no secrets are left behind for misuse. Auto-discover your global cloud estate to access. Audit and track every session.
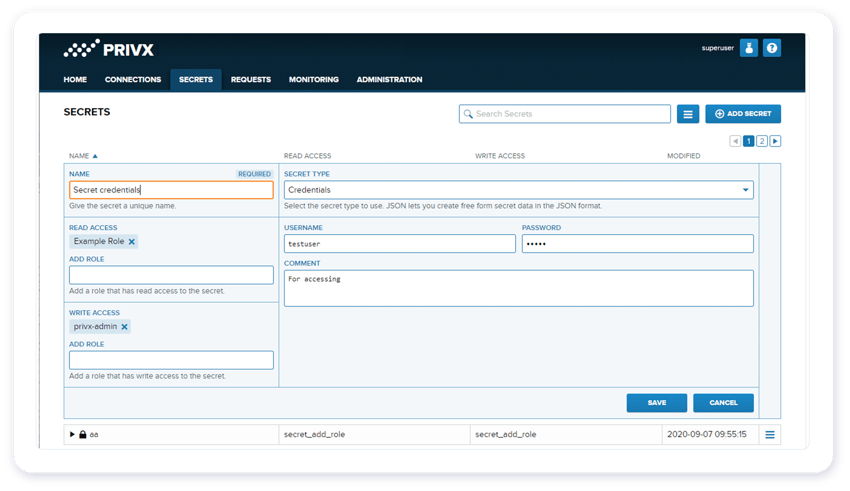
Secrets management for DevOps and automated sessions
Enforce least privilege and granular access controls for your machine-to-machine (M2M), application-to-application (A2A) and Robotic process automation (RPA) connections. Audit and track as needed.
Ensure your DevOps team secrets (passwords, encryption keys, API tokens) are protected. Comply with regulations with proper segregation of Duties (SOD).
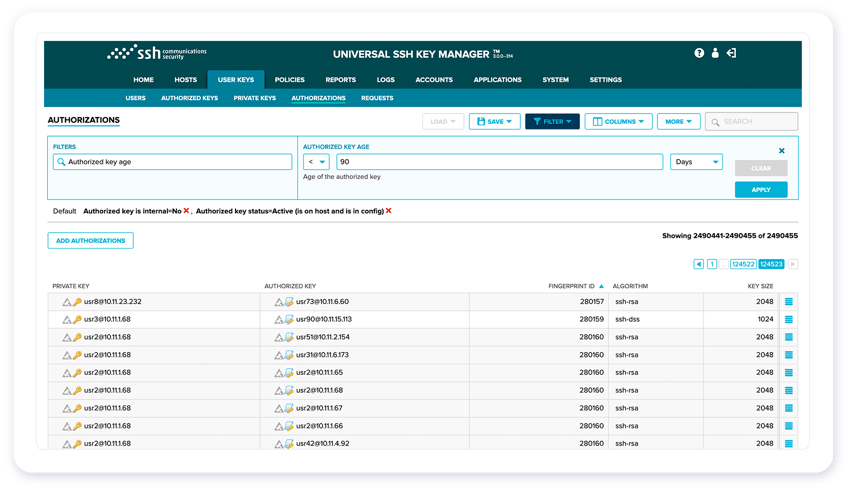
Mitigate risks, pass IT audits and stay compliant with your Secure Shell estate
SSH Keys, just like passwords, provide direct access to privileged accounts on critical infrastructure. Discover, manage and automate the use of hundreds-of-thousands of keys in large enterprises. Eliminate attack vectors, mitigate risks, pass audits and stay compliant with regulations.
Secure your SSH-based server-to-server connections (80% of all SSH traffic), prevent Privilege Access Management (PAM) bypass and misuse of untracked SSH sessions by 3r parties.

Remote access, file transfer and tunnelling protection for client/server and mainframe connections
Protect file transfers (using SFTP/SCP), encrypt application traffic and secure remote terminal connections. Comply with security standards, enjoy 24/7 support and reduce deployment and maintenance costs.
Ensure interoperability and business continuity with standards-based protocol. All flavors of Windows, Unix, Linux and IBM z/OS supported.
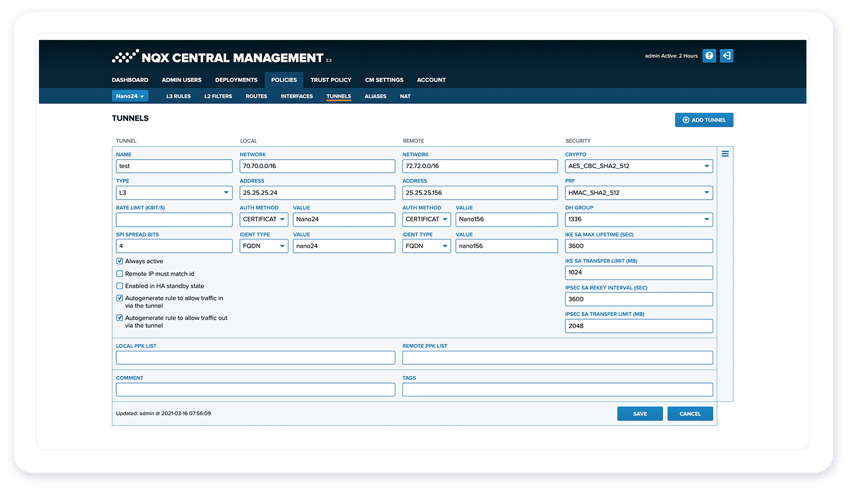
Quantum-ready protection on the network level for Ethernet and IP traffic
Apply state-of-the-art cryptographic protection against data leaks, breaches, misuse and interference for data centers, offices and sites.
Defend against advanced DDoS threats with persistent encryption that doesn't affect the performance of the connection when classified or mission-critical data is in transit.
Contact us
Do you have questions about our products or services? Would you like to find out about pricing, POC, or an enterprise demo? Don't be shy: get in touch and let's talk!







