SSH Quantum Security
Quantum computers are instant lock pickers
Quantum computers already exist and their power is increasing. Soon, they will reach the point where classical cryptography is in danger.
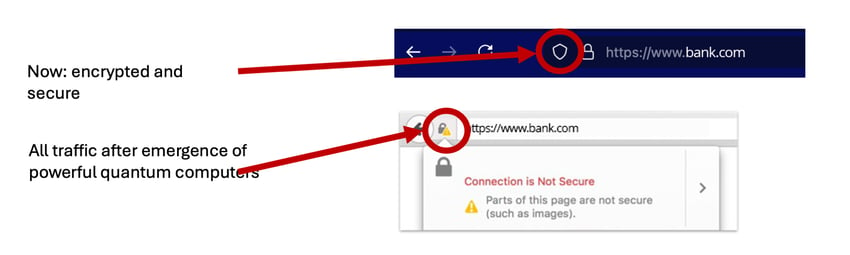
With more sophisticated quantum computing technology, all data encrypted with classic encryption is vulnerable. Encrypted traffic is already being captured and recorded - eventually, it will be possible to unlock the traffic when large-scale quantum computers will exist.
These locks are everywhere
Companies like Apple and Google are updating their solutions to quantum-safe (TLS) to protect web traffic.
We at SSH focus on securing:
- Critical networks that are based on IPSec and SSH
- Environments where you cannot upgrade the hardware
- Connections difficult to upgrade using in-house skills
- Large-scale data transmissions
- Long-term and sensitive secrets
Become quantum-safe now!
Organizations need to start their journey toward quantum security now. Quantum-safe cryptography (QSC) and post-quantum cryptography (PQC) are the backbones of quantum security.
“The rapid progress of quantum computing suggests the potential for adversaries of the United States to steal sensitive encrypted data today using classical computers, and wait until sufficiently powerful quantum systems are available to decrypt it. [...] a strategy for the migration of information technology systems of the Federal Government to post-quantum cryptography is needed.” - Quantum Computing Cybersecurity Preparedness Act, the US Congress
“In the United States post quantum cryptography isn’t just a good idea. It’s the law. “ – Gartner
It took 20 years to deploy current secure infrastructure at scale - start now.
Recommended and mandated by authorities
The following authorities and organizations are mandating or recommending for companies to start their quantum-safe journey now.
NIST and US Department of Homeland Security guidelines (2021)
U.S. Commercial National Security Algorithm Suite 2.0 (CNSA 2.0) advisory (2022)
EU Commission's PQC recommendations (2024)
Japan's Quantum Technology and Innovation Strategy (2020)
Monetary Authority of Singapore's advisory on quantum cybersecurity risks (2024)
Memorandum on federal agency migration to PQC (2022)
Quantum-safe journey
Quantum-safe technology and algorithms are developing rapidly.

SSH Communications Security quantum-safe journey
Embark on your quantum-safe journey together with us. We've been at the forefront of developing PQC portfolio for our products for years.

Our quantum-safe portfolio
PrivX PAM
Make Privileged Access Management quantum-safe with PrivX that supports new quantum-resistant SSH key exchange (KEX) algorithms for SSH connections.
Quantum security resources
GUIDE: Future-Proof Your Organization with Quantum-Safe Cryptography
Get the guide
EXPERT ARTICLE: Quantum Computing & Post-Quantum Algorithms
Read the article
EXPERT ARTICLE: Quantum-Safe Cryptography & The Quantum Threat
Read the article
BLOG POST: Why Quantum-Safe Privileged Access Management (PAM) Matters
Read the blog post
BLOG POST: You Don't Need New Fiber Cables to Be Quantum-Safe
Read the blog post
BLOG POST: How to Make Mainframes Quantum-Safe
Read the blog post







