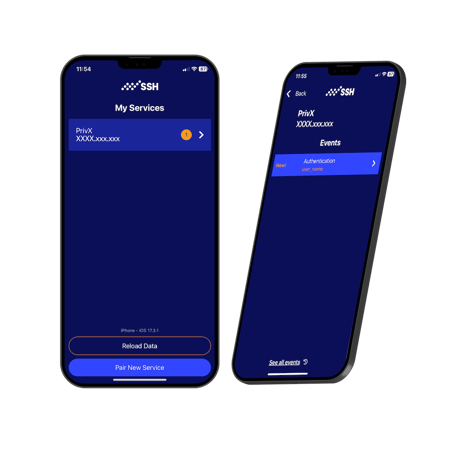
 Trust built-in from the endpoint
Trust built-in from the endpoint
to the critical target
-
IDENTITY. High assurance, phishing-resistant authentication.
- DEVICE TRUST. Real-time, continuous device trust, for every device.
- AUTHORIZATION. MFA and Authorization challenges Biometric authentication.
PrivX Authorizer is also a part of our modular SSH PrivX Zero Trust Suite.
Learn more here >>>
Eliminate the biggest attack vector
80% of breaches are caused by stolen credentials. Enable passwordless and keyless authentication to critical targets to ensure there are no credentials to compromise.
Put a stop to common MFA attacks
Man-in-the-middle, MFA fatigue, and token theft attacks are the most common methods to comprise MFA. Prevent them with strong ID authentication and robust encryption.
Continuous security posture validation
Validate user identity and device security posture throughout the session. Terminate at-risk connections automatically and add authorization challenges when needed.
Stay compliant
Track user access, connection history, and authentication events in an immutable audit record. Link verified-only devices to verified-only users if needed.
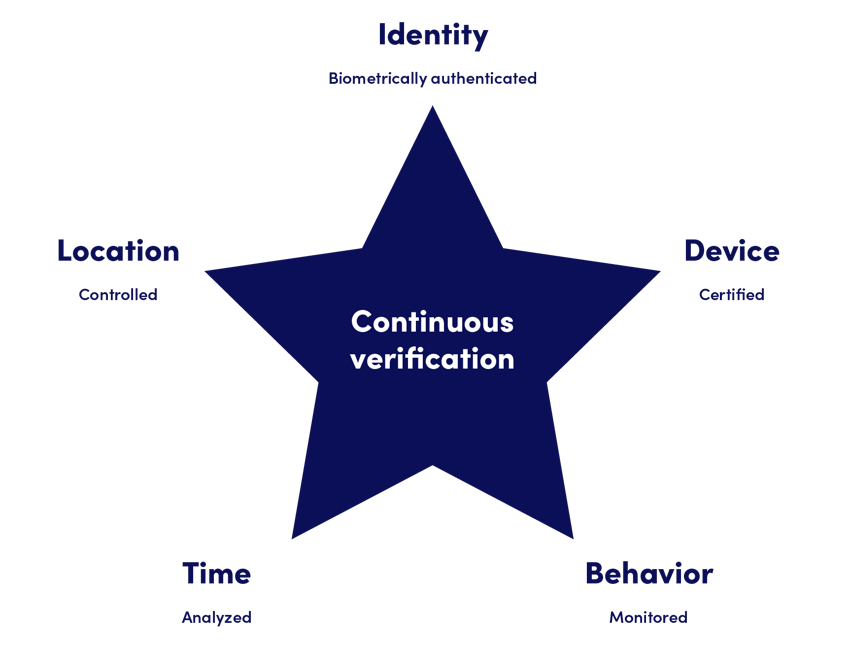
IdentiFive – beyond traditional MFA
PrivX Authorizer transcends traditional MFA or identity-only-based authentication tools.
By verifying identity, device, behavior, time, and location for each session, PrivX Authorizer creates a strong, phishing-resistant MFA solution tailor-made to access critical targets by high-impact users.
If any of the elements fail during authentication for the user or the device, the session request is denied or an additional verification is required. If the security posture of any of the elements changes, the session request is denied or an additional verification is required.
How does it work?
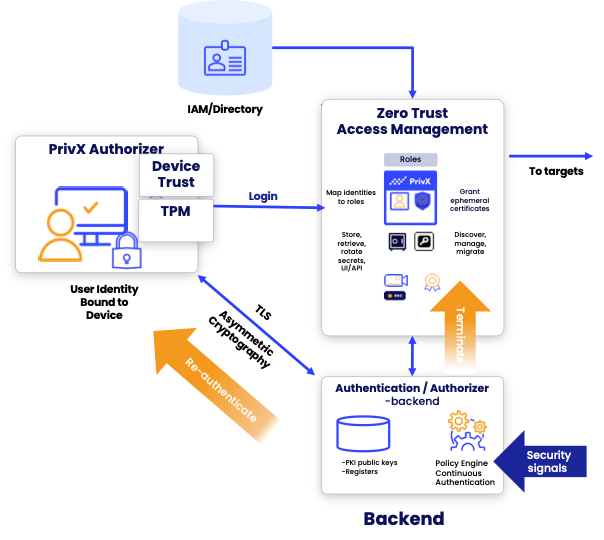
1. Strong authentication
Authentication based on a private key stored in the device’s keystore - a Trusted Platform Module (TPM). Add admin authorization if needed. No passwords or keys.
2. Biometric ID protection
Access to the TPM is protected by biometrics, meaning every time the private key is required for device authorization, the user is requested to
provide fingerprint or face recognition.
3. Strong encryption
All transactions are always verified and cryptographically protected with TLS.
4. Continuous validation
Continuously verify the legitimacy of the session and device in case of anomalies or unwarranted privilege escalations.
5. Access to the target
The right identity to the right target with the right level of privileges to get the job done with PrivX.
6. Track, audit, and monitor
Get an audit trail of activities on individuals, record sessions if needed or monitor them live.
Journey to phishing-resistant authentication
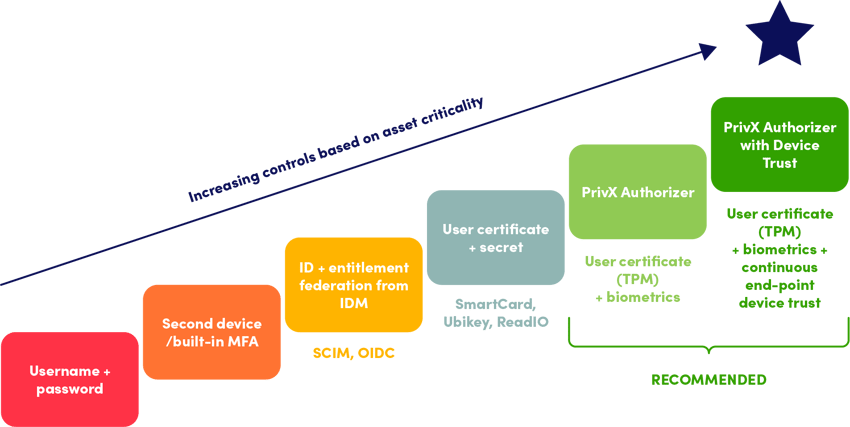
Username & password: No MFA. Not recommended.
Second device authentication or built-in MFA: Offers the minimum level of MFA for low impact targets. Users have a separate account per application.
Centralized ID control: Users no longer have their own accounts for each individual application, but identities are centrally managed from an identity management system (IDM).
FIDO2 or smart card: Adds password validation with FIDO2, passwordless authentication, or authentication with a smart card that is often bound to a security module of the user's device.
Biometric authentication: Adds a Trusted Platform Module (TPM) protected by fingerprint or facial authentication. Allows admin authorization for sessions using an external device.
Device trust: Adds continuous session monitoring and the security posture of the end device. Terminates at-risk connections automatically, for example, if the virus scanner of the device is down.
Authorities on MFA
NIST
Phishing resistance for a given subscriber account is only achieved when all methods of authentication are phishing resistant.
NIST SP 800-63B-4
CISA
CISA strongly urges all organizations to implement phishing resistant MFA to protect against known cyber threats.
Implementing Phishing Resistant MFA
OMB
Agencies must require users to use phishing-resistant method...necessitated by reality that enterprise users are among the most valuable targets for phishing.
US President M-22-09
See the solution in action
Contact us by filling in the form >>>



