SSH Keys are critical credentials like passwords
Secure Shell (SSH) access is everywhere within your IT environment. It is the de-facto method for Linux, database & network admins and application support teams to securely connect to servers and applications within them - whether they are on-premise or in the cloud.
SSH grants access to, for example:
- credit card and medical data
- tax records and Intellectual Property Rights (IPR)
- CI/CD pipeline and provisioning tools (Ansible, Chef, Puppet, Bladelogic)
- cloud servers and containers or firewalls and network devices
Just like passwords, SSH keys are an access credential in the SSH protocol. What's more, 80% of SSH connections are used for automated tasks and over the decades, the number of encryption keys in IT environments has skyrocketed.
SSH Keys pose a risk - but are often forgottenSSH keys are credentials, just like passwords, as they provide access to privileged systems and accounts that if compromised can lead to unauthorised access, bypassing security systems & maliciously traversing IT systems unchallenged.
The implied risks associated with this compromise is customer data & IP theft, critical service outages and increased exposure to ransomware attacks.
Just like passwords, SSH keys are an IT audit failure point and their ungoverned use is against multiple regulations.
Many organisations have put considerable effort into ensuring that passwords are rigidly governed and brought under control, yet the management of SSH keys is often overlooked.
The sobering news is that even if a large organization has all their privileged passwords under control, if their keys remain ungoverned, in the worst case scenario, they have only 10% of their access credentials managed.
Based on our experience, SSH keys are often 10 more common access credentials than passwords in IT environments.
SSH keys accumulate over the years and must be managed
Large enterprises typically need to provision and control tens of thousands of SSH connections across their server estate on a monthly basis. This is because SSH encryption keys do not expire by default and are rather easy to create to complete a specific task by anyone with rudimentary IT skills.
Since IT personnel can self-provision SSH keys, their use is also de-centralized. Most business lack a centralized view and the capacity to manage keys in a systematic fashion for this very reason.
Over decades, the key numbers in IT environments skyrocket.
Enterprises without a proper SSH key management solution in place will have operationally inefficient processes for the following:
- Provisioning SSH keys or fixing misconfigured access
- Removing SSH access that is no longer required
- Renewing key pairs to maintain compliance
- Ensuring security access management systems are not bypassed
Organizations have attempted to solve the SSH key challenge in-house. But they are often surprised with the complexity of the problem, since there's no central governance over the keys and their numbers are often measured with hundreds of thousands. They often simply give up.
This is where specialized software like our Universal SSH Key Manager steps in. It discovers even the hardest-to-find SSH keys from massive enterprise encryption key estates and centralizes their management without requiring changes to the key architecture.
In short, does the heavy lifting for the customer and it puts them in charge of their critical but often forgotten credentials.
This is one of the reasons why many Fortune 500 have chosen to collaborate with us to solve the key problem, even when they have other security solutions like Privileged Access Management (PAM) in house. PAMs alone simply cannot manage keys at enterprise level, often covering only 20% of all case - in the best case scenario.
Keyless SSH radically reduces management complexity
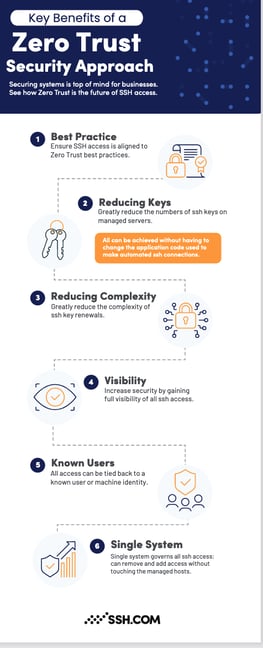 Even with a great SSH key management solution in place, SSH key management processes can be complex and challenging - especially in highly dynamic enterprise environments.
Even with a great SSH key management solution in place, SSH key management processes can be complex and challenging - especially in highly dynamic enterprise environments.
We see the future of SSH access following Zero Trust principles. It's a paradigm shift where you no longer attempt to manage static SSH encryption keys but instead migrate to just in time (JIT) certificate-based authentication.
In this model, access is granted on-demand at the time of establishing the connection. Instead of using keys, access is granted with short-lived certificates that are invisible to the user and that expire automatically after the connection. This means that there no longer are any permanent SSH encryption keys left behind to be managed.
This is a huge evolutionary step for Enterprise Key Management. We call it SSH Zero Trust access that has the following benefits:
- Greatly reducing the need to manage static SSH keys - often reducing their numbers by the thousands
- Significantly simplifying the key rotation process with less keys to rotate
- Enabling session recording and full visibility of the SSH connection
- Full audit and control of SSH connections - including machines
Zero Trust SSH is an evolutionary leap in Enterprise Key Management
Zero Trust strategies are essential for ensuring a better security posture which also includes SSH access. Whether on-premise, in the cloud or a hybrid environments, Universal SSH Key Manager discovers and manages SSH keys to assure compliance.
But Zero Trust proof UKM takes the game to the next level. It radically reduces the complexity and management overhead in SSH key-based authentication. With UKM Zero Trust, organisations migrate from managing thousands of key to a future-proof Zero Trust SSH access without keys - at their own pace.
Learn more about UKM Zero Trust here or check out the Buyer's Guide for Zero Trust Enterprise SSH Key Management below.
Marieta Uitto
Marieta Uitto is a product manager currently focusing on driving roadmap and collaboration with customers to successfully solve their challenges. She has spent over 15 years with SSH.com of which more than ten, working in R&D with exceptional teams to deliver industry leading products. PAM solutions, Key Management...

